Author – Varun Raval, Cloud Engineer Intern
 As mentioned before, you need a Log Analytics workspace to work with Azure Sentinel. You can also create a new log analytics workspace by:
As mentioned before, you need a Log Analytics workspace to work with Azure Sentinel. You can also create a new log analytics workspace by:
 By clicking on “Open connector page” of the data sources you can connect the particular data into Azure Sentinel. You connect as many as you can as long as they are relevant to your environment. There are various connectors not just from Microsoft, but also from third party providers like Palo Alto, Check Point, Cisco ASA, Fortinet, etc.
Every configuration wizard has different settings. Here is an example of Azure AD. You can configure Azure Sentinel to connect the Sign-in logs and Audit logs from Azure AD.
By clicking on “Open connector page” of the data sources you can connect the particular data into Azure Sentinel. You connect as many as you can as long as they are relevant to your environment. There are various connectors not just from Microsoft, but also from third party providers like Palo Alto, Check Point, Cisco ASA, Fortinet, etc.
Every configuration wizard has different settings. Here is an example of Azure AD. You can configure Azure Sentinel to connect the Sign-in logs and Audit logs from Azure AD.
 Note that to integrate with Azure AD alerts:
Note that to integrate with Azure AD alerts:
 Let’s look at these parts in little more detail:
Let’s look at these parts in little more detail:
 These playbooks can be triggered either manually or automatically when an alert is fired in Azure Sentinel. In a single playbook, you can trigger one or more actions taken together in an automated way.
These playbooks can be triggered either manually or automatically when an alert is fired in Azure Sentinel. In a single playbook, you can trigger one or more actions taken together in an automated way.
Overview
Azure Sentinel is Microsoft’s cloud-native SIEM (Security Information and Event Management) service with built-in AI analytics. Threats related to infrastructure, networking, users, and applications can be monitored via Azure Sentinel. As a cloud-native service, it works as per your requirement. It collates the data from your on-premises Azure environment, and any third party cloud providers. It uses Microsoft Threat Intelligence to analyze and filters out the noise from actual alerts. Azure Sentinel drills through all the incoming data and performs analysis based on different known patterns like anomalous logins,etc. It makes sure that you get a view of all the relevant security information that are required to draw your attention to the specific alert. The key pieces of information that you get right away are:- Number of total Alerts
- Total Events collected and analyzed
- All the total active Cases and their split by status
- Map view of the potential malicious activities and events
Steps to Build and Configure Azure Sentinel
1. Creating an Azure Sentinel
To start working with Azure Sentinel, you can create it by:- Clicking on All Services
- In the search panel search for “Azure Sentinel”
- Clicking on the Azure sentinel which has occurred on the search result
 As mentioned before, you need a Log Analytics workspace to work with Azure Sentinel. You can also create a new log analytics workspace by:
As mentioned before, you need a Log Analytics workspace to work with Azure Sentinel. You can also create a new log analytics workspace by:
- Clicking on the “+ Add” button on the top left side, or:
- You can Connect one of the existing Log Analytics workspace as well
2. Connecting data connectors in Azure Sentinel
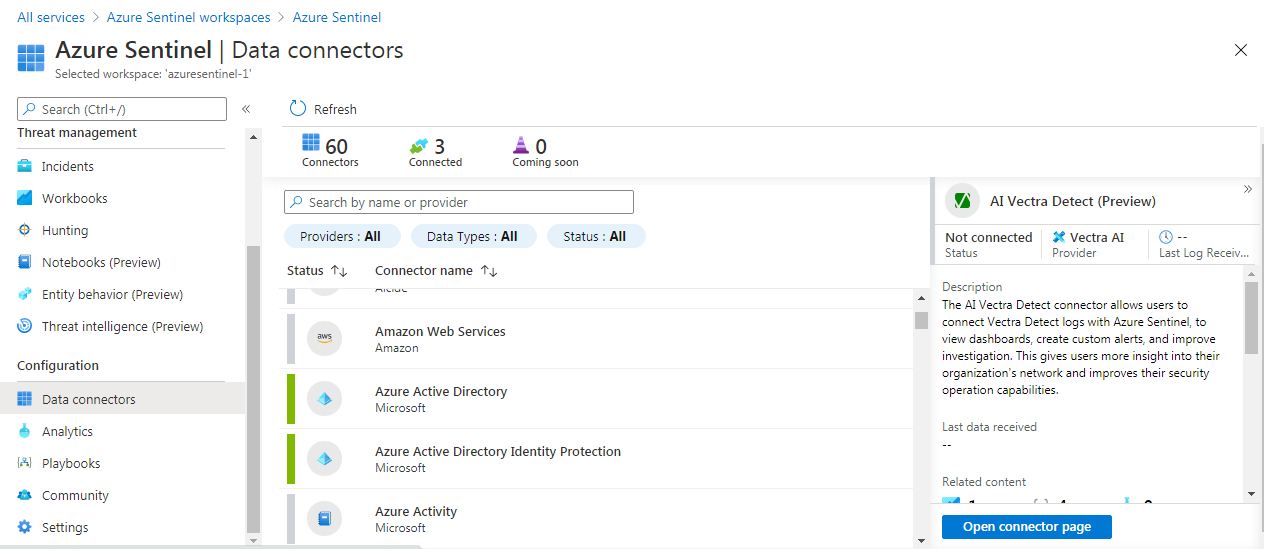
Once you have created an Azure Sentinel, you will need to connect data sources. You can connect the data in Azure Sentinel from the “Data connectors” option under the Configuration settings. By clicking on “Open connector page” of the data sources you can connect the particular data into Azure Sentinel. You connect as many as you can as long as they are relevant to your environment. There are various connectors not just from Microsoft, but also from third party providers like Palo Alto, Check Point, Cisco ASA, Fortinet, etc.
Every configuration wizard has different settings. Here is an example of Azure AD. You can configure Azure Sentinel to connect the Sign-in logs and Audit logs from Azure AD.
By clicking on “Open connector page” of the data sources you can connect the particular data into Azure Sentinel. You connect as many as you can as long as they are relevant to your environment. There are various connectors not just from Microsoft, but also from third party providers like Palo Alto, Check Point, Cisco ASA, Fortinet, etc.
Every configuration wizard has different settings. Here is an example of Azure AD. You can configure Azure Sentinel to connect the Sign-in logs and Audit logs from Azure AD.
 Note that to integrate with Azure AD alerts:
Note that to integrate with Azure AD alerts:
- You must have a Global Administrator or Security Administrator permission in Azure AD
3. Understanding Azure Sentinel Dashboard
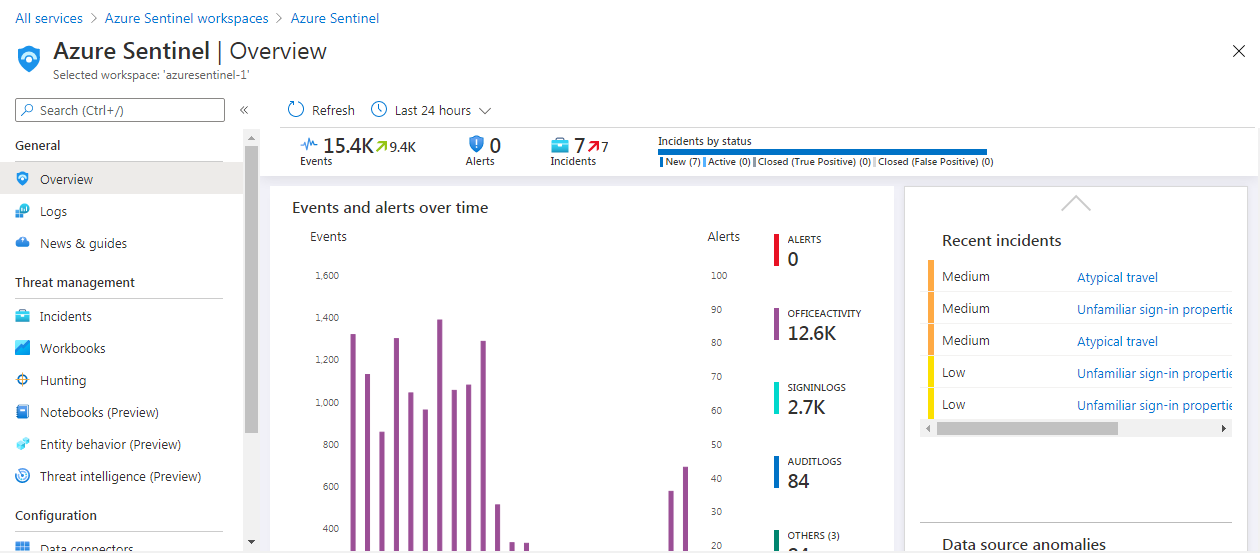
When you start your Azure Sentinel the dashboard will look something like the below image. Let’s look at these parts in little more detail:
Let’s look at these parts in little more detail:
- First, you have all the settings and various sections related to Azure Sentinel
- Next, you have the key details in nutshell at the top
- A graph of events and alerts over time is shown
- Any malicious events are mapped on the world map
- On the right, you have all the recent cases listed
- Data sources anomalies are graphed below the recent cases block
- This last section on the right shows you the Machine Learning capabilities related to Azure Sentinel
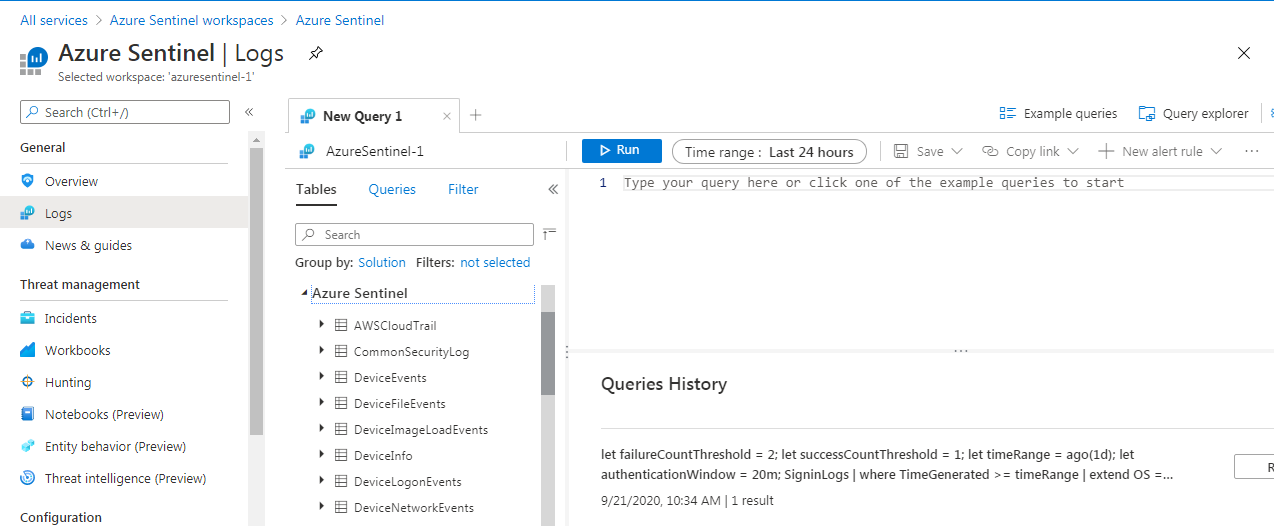
4. Running Queries in Azure Sentinel
Azure Sentinel uses the KQL query language same as Azure Log Analytics to run the query. You can use this to analyse your security data. There are multiple sample queries available for you or you can write your own custom query as well. Below is an image of the Azure Sentinel Logs interface, where you can write and configure your queries.
- You can access the queries by navigating to the Logs section.
- You can create multiple tabs, one for each query, to work on the queries simultaneously.
- Next is the section where you actually write your query. Once you have built your query you can click on the “Run” button to execute the query.
- You can inspect all the workspace in your environment in the section on the left. You can also click on any source and can expand it to see information under it.
- There are various sample queries provided which you can use.
- Finally on the right is the section for documentation, query language reference, and other useful information.
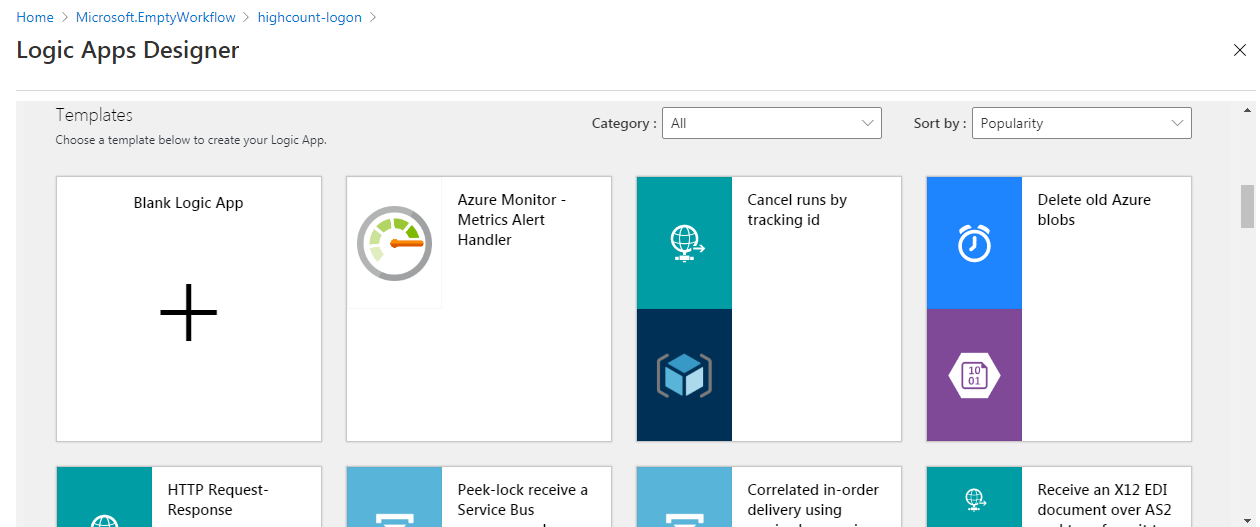
5. Automating Operations with Playbooks
You can build and run Playbooks in Azure Sentinel to generate automated response against various alerts. Playbooks are Azure Logic Apps workflows that you can easily create in the Azure Sentinel. You can create playbooks for various scenarios, such as:- Blocking an IP address from where an attack may originate
- Resetting a User password
- Opening a Ticket in your ticketing system
- Blocking access to a Virtual Machine on a particular port
- Shutting down a Virtual Machine
- Sending an email notification
 These playbooks can be triggered either manually or automatically when an alert is fired in Azure Sentinel. In a single playbook, you can trigger one or more actions taken together in an automated way.
These playbooks can be triggered either manually or automatically when an alert is fired in Azure Sentinel. In a single playbook, you can trigger one or more actions taken together in an automated way.
Other Features
There are various other features in Azure Sentinel. In brief, these features are:- The Investigation Tool helps you understand the scope and root cause of a particular threat. You can drill down into the data for any event you want to investigate.
- Azure Notebooks are free hosted service to develop and run Jupyter notebooks in the cloud without installation. It allows you to look into common investigative steps.
- Hunting lets you use pre-built queries which are crafted by Microsoft security experts. This makes Azure Sentinel more advance tool as compared to the other features. This helps you hunt for anomalies and security threats across your organization.
- Azure Sentinel on GitHub hosts various community provided resources, like sample Dashboards. Visit the official GitHub page at https://github.com/Azure/Azure-Sentinel.